Blockchain technology appears to be the most promising in terms of security and efficiency in today’s times, owing to the consistent advancement of technology. In simpler terms, a blockchain is a network of several nodes that validate transactions and store the data in a public ledger. And what’s the catch? The data on the public distributed ledger cannot be tampered with or mutated, thereby strengthening security.
Look at how transactions are carried out on the blockchain, where smart contracts play a role, security of smart contracts. What does it all mean?
What Are Smart Contracts ?
Smart contracts are programmed instructions coded with functions and data that are used to execute transactions on the blockchain. When a user requests a transaction, the smart contract checks to see if the buyer and seller conditions have been met.
After validation, it automates the transaction without the use of any intermediaries. As a result, it is crucial to ensure the security of smart contracts; their insecurity frequently leads to substantial financial losses.
What Are the Potential Security Threats to Smart Contracts?
Smart contracts indisputably make the show run on the blockchain, so they must be extremely secure. However, smart contracts are sometimes vulnerable to security attacks. Below is an attempt to list all of the kinds of attacks that smart contracts are exposed to.
Smart contract issues are broadly classified into three types:
Operational risks With poor network governance, operational risks occur at the authorization feature level. As a result, assets’ functionality is altered; burning or self-destruct functions are activated, and so on.
Implementation risks associated with smart contract implementation, such as unauthorized transfers.
Design risks occur when default features are mishandled, causing the intended execution of smart contracts to change. This can lead to untrusted control flow, asynchronous transaction processing, and other issues.
How Should Security Issues in Smart Contracts Be Handled?
Here are a few strategies for dealing with the security risks that smart contracts must deal with.
- Code the smart contract in the best programming language possible.
- Periodic penetration testing to audit the security of smart contracts and determine if they are vulnerable to threats.
- Adhere to the blockchain security checklist.
- Using automated vulnerability scanners to keep track of security breaches.
- Monitor the blockchain and smart contracts using security audit tools.
- Identify and mark any untrustworthy contracts.
The Process of Smart contract auditing
Gathering details: All smart contract specifications are gathered in one place in order to understand their intended concept. Smart contract auditing firms accomplish this by having clients fill out forms with project-specific fields.
Contracts are manually tested: The code provided in the contracts is reviewed line by line to ensure that it serves the intended purpose. Manual tests are run to identify common discrepancies such as overflows, service denials, and so on.
Run tests with automated tools: “To err is human,” as the saying goes, and automated tools are used to detect errors that are missed during manual testing.
What Security Tools Are Available for Smart Contracts?
It is essential to deploy security tools for smart contracts in order to minimize or eliminate errors while functions are being executed.
- Oyente – To detect common flaws in smart contracts.
- SmartInspect – Analyzes smart contracts using decompilation techniques.
- GasTap – Protects against gas vulnerabilities.
- Securify – An online static analysis tool that provides security information on vulnerability patterns.
- Vandal – A static security analysis framework that converts smart contract bytecodes to logic relations.
- Ethereum graph debugger – An EVM debugging tool that visually analyzes the entire program.
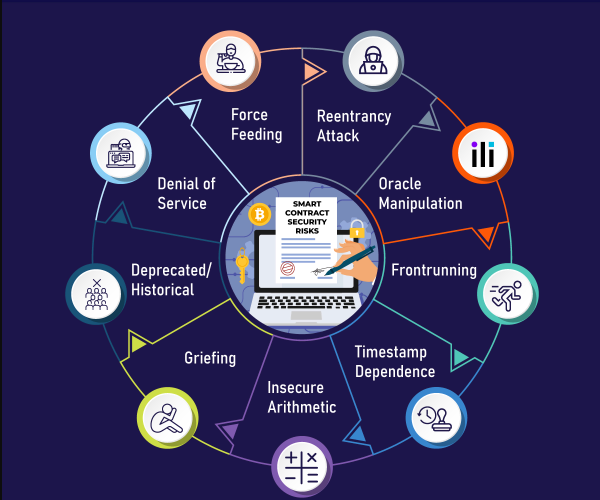
Risks of Smart contract security
The list of known security risks is the most striking feature in any smart contract security guide. In order to ensure smart contract security, you must be well-versed in the most common attacks. Here are some of the most serious threats to smart contract security.
Reentrancy attack
Reentrancy attacks are visible when exploiters can call functions multiple times before the first invocation ends. The reentrancy bug can be used by malicious agents to withdraw balances multiple times.
Oracle Manipulation
Manipulation of external data providers, as well as possible solutions for Oracle security issues, would have an impact on smart contract security.
Frontrunning
Frontrunning attacks could imply malicious use of blockchain technology’s transaction processing approach.
Timestamp
The best practices for smart contract security would also include a discussion of timestamp dependency. It is generally responsible for attacks involving the timing of a transaction.
Uncertain Arithmetic
Integer overflows and underflows pose yet another significant security risk for smart contracts. Insecure arithmetic can also lead to vulnerabilities that allow attackers to create novel logic flows.
Griefing
One of the most notable features of smart contract security tools is the resolution of griefing. Such attacks are associated with bad actors within the system.
Deprecated/Historical
Deprecated/historical attacks are linked to the Ethereum blockchain’s history and vulnerabilities. Such smart contract security issues can be solved at the compiler level.
Denial of service
Smart contract security issues with denial of service attacks typically show unexpected reverts in addition to an increase in block gas limits.
Force Feeding
Force-feeding is another significant smart contract security risk to be aware of. It works by forcibly transferring Ether to smart contracts in order to manipulate balance checks.
Best Practices for Smart Contract Security
The collection of smart contract security tools and the advantages of audits can only take you so far in securing smart contracts. Smart contract security is not a primary objective. On the contrary, it is a methodology, and you must be prepared for dynamic changes in the smart contract landscape. Smart contract applications are changing, as are the principles underlying their operation and security. Here are some of the best smart contract security practices.
- Prepare for failure at all times and strive to make your code as resilient as possible with each attempt.
- One of the trusted practices for dealing with smart contract security issues is to keep track of new security developments.
- Another simple practice to avoid smart contract security risks is to keep smart contract logic and code simple.
To the End ,
Smart contracts are becoming well-known for their trust, precision, and cost-efficiency as technology rapidly shifts to blockchain across various sectors such as health care, supply chain, finance, and so on.
Though they are far superior to traditional legal contracts in terms of security, they are not without flaws. As a result, it is becoming increasingly important to use the best possible methods to ensure that they are resistant to security attacks while coding.